In my previous post I wrote about the key Cyber Security threats that individuals and businesses of all sizes face. If you’ve not read it you can catch up here.
This time around I am going to review some of the key protective measures that you can take. Measures that will make your business harder to defraud, harder to hack and less likely to fall victim to Cyber Crime.
Let’s start with your website. Hackers around the world are queuing up to take over your website or to simply to bring it too it’s knees to stop it working so they can demand money to restore it to good working order. This latter approach is a Distributed Denial of Service attack – aka DDoS. (My previous blog describes a DDoS so I won’t replicate the description here, for brevity).
How do you stop a DDoS attack from bringing your website down
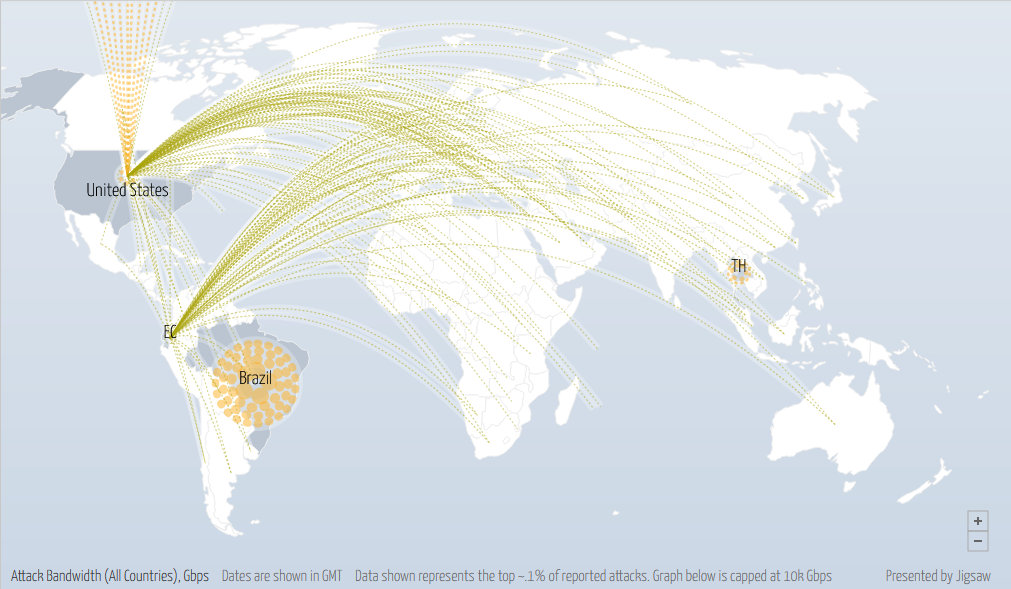
DDoS attacks are happening all around the world, right now, as you can see from this Cyber Attack screenshot
There are two approaches. You can choose a web host that has the necessary provisions in place to ensure that they have the connectivity and technology to make sure that DDoS attacks can’t prevent their web servers from running. They will use a variety of technology, including sophisticated firewalls, traffic filtering and DDoS defence systems. Not all web hosts offer such a high security level so you’ll have to shop around.
A better option, in my opinion, is to use a Content Delivery Network (CDN). A CDN uses many servers located around the globe. This means that if a single server location is targeted regular visitors are simply directed to the next nearest server, totally mitigating the threat. Another big benefit of CDNs is that they also mean that if your website targets different countries then visitors from those countries will connect to your web server that is closest to them – which ensures that your website is always delivered at the fastest possible speed – which benefits both the visitor and your SEO because no-one, not least Google, likes a slow website. Top CDNS are Cloudflare, Amazon Cloudfront and Microsoft Azure
Passwords
I know, I know, I am always banging on about Passwords but passwords are gateways in to PCs, Phones, Networks, your web host and so much more.
So, your gateway passwords needs to be really secure if you want to keep the hackers out – and you really do want to keep them out. You might think that there’d be no interest in your website but hackers are targeting every single website they can find. The UK’s National Cyber Security Centre recommend using a password comprising of 3 random words and a unique password for every site you access. I recently made a short video about this very topic
Firewalls
A Firewall provides an impenetrable, unhackable barrier (provided it’s properly configured) between the internet and your computer or computer network.
Yes, Windows has a Firewall and it’s certainly better than having no firewall at all but, in reality, it’s about as much use as a chocolate fireguard. It’s just too easy to misconfigure, especially if you have a small network and have fiddled with the settings as you try to share files and folders from one PC to another.It might deter the casual hacker but won’t stop a determined one.
There are software firewalls that are provided by the same companies that sell anti-virus software. These are better than the Windows firewall but similar issues remain. Each device on your network has to have one installed and kept up to date.
A far better solution is to use a firewall appliance. A little box that goes between you, your internet router and the internet.
And talking about your router, the device that was supplied to you by your broadband provider. The router does include a Firewall but it’s a tad rudimentary, at best, and if you have’t set a secure password it will still be using the password and user name that it shipped with. This could be as daft as having “admin” as both the user name and password which makes as easy to access from the internet as it does from inside your home/home office or office.
And all somebody has to do is Google the make of router that’s used by broadband company X and the default user names and passwords are readily available. Targeted at those who might have lost their user manual but available to all.
These types of firewall are about as much use as a wall made of paper if you are running a business. It’s much better to invest in a dedicated firewall appliance.
The most popular are provided by Watchguard, SonicWall, Cisco and these prevent computers and networks from a wide range of Cyber attacks.
My set up looks like this. My office provider uses a Watchguard firewall in their comms room. I have a D-Link firewall in my office AND use the Windows firewall on my computers
VPN

Imagine the scenario. You are in your favourite coffee shop and need to jump on their free Wi-Fi. You spot the password on a tent card on your table and fire up your laptop/Chromebook/tablet/phone and search for the Wi-Fi. There it is, right at the top “FreeCoffeeShopWiFi”. You click, you enter the password and you’re away.
You log in to your office email account, then your private email. Then a quick check of your bank account confirms that you have enough to buy that latest thing you’ve been after.
Later that day you check your emails. There’s an unexpected one from your favourite shopping site confirming a change of password – not something you remember doing – so you check your bank account. It’s empty, drained of everything while you were finishing your coffee.
What’s happened? When you logged in to the coffee shop WIFI you weren’t logging in to the legitimate account. Somebody had set up a clone inside the coffee shop, which you found and logged in to. The person behind the clone was “sniffing” all of the traffic going through their portable WiFi hotspot that they’d set up and were merrily pulling off websites, user names and passwords and happily started to spend other people’s money, including yours. This is known as a man-in-the-middle attack.
Could you have prevented it? EASILY.
Just get yourself a VPN, they’re inexpensive but provide a very secure way to access the internet. Simply put, a VPN creates a secure, encrypted, private tunnel between your device (phone/tablet/laptop etc) and the destination website, (bank, email account, online shopping site etc). It doesn’t matter whether you are on a genuine account or a cloned account, your tunnel can’t be broken in to, your data is secure.
Another use of VPNs is when you work remotely and needs to access office files, remotely. A VPN will secure the data that moves between your office and your device and keep everything safe.
You might also use your VPN at home, just in case your neighbour is on your WiFi and “sniffing” your data.
And, finally, if you want to appear to be in a different country – let’s say you are on holiday abroad and want to watch BBC iPlayer content that is only available in the UK – you can use a VPN to give you a “point of presence” in the UK. Your VPN makes it look as though you are in the UK when in reality, it’s just the end of your VPN connection.
If you subscribe to a Google business service then you have free access to a Google VPN on your phones and tablets. If you don’t want to use that then some of the best are provided by ExpressVPN, TunnelBear and StrongVPN.
I use TunnelBear but am not an affiliate so if you sign up, there’s no benefit to me just added security for you
Not clicking
Phishing, SMSmishing and SpearPhishing emails are mainly designed to make you click on a link to visit a genuine looking but fake website where your log-in information can be harvested.
I’m going to be blunt – DON’T CLICK. If you think the email may be genuine you can either contact the sender (by phone or with a fresh email – not a “reply”) and ask them for clarification. If it’s a link to a website then enter the domain name yourself in your web browser, don’t click on the link in your email, don’t “copy” the link but DO hover over the link in your email program (it will have been designed to look legitimate) but hovering your cursor over it will show you where the click will actually go. It might look similar to the pukka site but won’t be. If the proper URL is company.com the fake address could look like company.com.fakesite.eu or company123987.com, for example.
Even if you believe the link to be valid, don’t click on it but either enter a URL you KNOW in your browser or search for the company. 99% of the time you’ll see that that your email is a fake, an attempt to extort you.
Fake News and Fake Reviews
Although you can’t prevent third parties from posting Fake News and Fake Reviews about your company, you can be on the lookout for the posts so you can take remedial action. Use tools such as Google Alerts and Drumup.io which can conduct keyword searches for your brand and alert you by email when something turns up that uses your brand or company name. Then you can see where the article has been posted and review it. If it’s obviously fake news you should post a reply AND contact the host of the review platform and advise them of this
Hacking
What can you do to prevent your devices and networks from being hacked?

You can use a Firewall to provide a secure “wall” between your network and the outside world. You can make sure that you have changed the default user-name and password and use a hard to crack password – something like the three random words recommended by the National Cyber Security Agency.
You should use biometric access controls, fingerprint or facial recognition on your phones, tablets and computing devices. You should be wary of emails and their attachments.
Ensure that your anti-virus programs are up to date and that Windows is allowed to keep itself up to date too.
You should consider encrypting your data, so if it is stolen then it won’t be of any value, or use, to anyone and you also need to be regularly backing up your computers and servers. AND don’t forget to regularly check that you can restore your backed up data. There’s nothing like finding out that your backups are corrupt, or discovering that you’ve not been backing up what you thought was being backed up, when you lose data. It’s too late then.
And finally, train your staff and keep their training up to date so they know how to identify potential threats and to whom they should share their concerns with.
Insider Threats

Insider threats are the most insidious. By definition, it’s people who you trust. So what can you do?
You should control what they have access to. Nobody outside the Accounts department (with the exception of some board members) needs to have access to financial systems, and files. Nobody outside of Sales needs to have access to details of ALL clients at all stages of the sales process. Give a lot of thought to who can see, and access, what.
Work hard to know your staff. Talk to them. Understand what makes them tick, their personal situation, without being creepily intrusive. Join conversations “around the water cooler”. Have an “open door” policy so that your people know they can bring their concerns to you.
You should also have a very clear policy on BYOD (Bring Your Own Device) where people are permitted to use their personal phones, tablets and laptops and can connect them to the company networks and Wi-Fi. Yes, it’s a great way to save money by allowing people to use their own equipment but it opens up a whole host of risks.
- What are they taking home with them to “work” on?
- What websites do they visit during work time whilst connected to the company network?
- What security protection are they using on their private devices?
- What Social Media platforms are they on whilst in company time and on the company network
- What policies are in place to manage their use of external memory devices (such as USB sticks and external hard drives)
- What files and folders can they access
Ultimately, you might decide that the risk is not worth the saving and simply provide all the equipment and tools that your people need to be able to do their job.
USB Memory

As discussed in my previous Post, “Top Cyber Security Threats to YOUR Business“, USB storage devices can be an absolute nightmare. You must have a policy in place that covers how they are used. How/whether your employees can use their own, what the policy is in relation to found devices. How you will manage lost devices that might have company information on them and an overall policy with regards to USB ports.
I know of many companies that have simply banned the use of unauthorised USB connections (remember, connecting a phone or tablet to charge it means that device can also be used as USB storage to remove data or introduce a virus).
I even know of one business owner who used superglue to ensure that absolutely nothing could be plugged in to the majority of computers and servers in his business. Even I agree that that was an extreme solution but I get his point.
Ransomware
Ransomware normally arrives either as an attachment on an email or via a link contained in an email so, good email security and data hygiene will minimise the risk from this threat
Viruses, Trojans and other Malware

Again, most viruses and trojans infiltrate a business via attachments on Emails and links in emails. The attachments might look like PDFs, Word or Excel documents or pictures but they won’t be. They will either have embedded macros (Word, Excel etc) or mask their true type. Something that looks like picture.jpg might actually be picture.jpg.exe – a file that will be run when clicked rather than a nice picture that will open when clicked.
And rogue USB devices remain an ever present threat.
Avoiding a lot of these threats comes down to good email security and data hygiene although this will be reliant on good training, regular updates and reminders.
You might have a decent anti-virus application running on all devices (including phones and tablets) but it’s a constant war. The cyber criminals are always on the lookout for ways to circumvent security software so you still need to be alert to the threats.
And Ditch Microsoft Windows
Yes, I know. It sounds almost like heresy, but Microsoft does have a bit of a reputation for insecurity. Yes, it’s better than it was but, as the most popular operating system, it’s also the most popular target for hackers. It even has it’s own day of the week – Patch Tuesday, when all manner of updates are released, including security fixes. Apple Macs are better. However, as sales increase so does the hackers interests and it’s not as secure as some would like you to think.
So is there a solution?

Yes, it’s called Linux. It’s been around more than 30 years, is properly free and very secure.
But don’t you have to be a bit of a geek to install, and use a Linux machine?
Nope, not these days. For most, it’s as easy as installing Windows AND it even looks, and works, a lot like Windows because that’s what we’re all used to. I run a Linux machine in the office and it’s uses Linux Mint – which is probably one of the easiest to come to terms with. And you can learn more about Mint, download it and learn how to install it here. Another popular Linux distribution is from Ubuntu and you can run Ubuntu from a USB stick if you want to give it a try without installing – oh and you can also create dual-boot scenarios where you can keep Windows, install Linux and simply choose which one you want to run when you boot your PC.
I am not a cyber security expert although I’ve done my fair bit, especially when working in IT support, and I do my best to stay up to date so feel free to send any questions you might have to andy@enterprise-oms.co.uk or give me a call on 01793 238020 or 07966 547146, Tweet me @AndyPoulton or contact me on LinkedIn and if I can’t help, I know some real cyber security experts that I can put you in touch with.
Thanks for reading and if you need help with your #SEO or any other element of of your digital marketing, please don’t hesitate to get in touch.
Andy Poulton
Chief SEO Officer
Enterprise Online Marketing Solutions


















 Last year, Brian Dye, Senior Vice-President for Information Security at Symantec (the company behind Norton Anti-Virus solutions) said, in an interview with The Wall Street Journal, that “Anti-Virus is dead”. What he meant was that cyber criminals were now able to write malicious software faster than Norton could be updated.
Last year, Brian Dye, Senior Vice-President for Information Security at Symantec (the company behind Norton Anti-Virus solutions) said, in an interview with The Wall Street Journal, that “Anti-Virus is dead”. What he meant was that cyber criminals were now able to write malicious software faster than Norton could be updated.