In other words, have you been pwned*. There have been millions of email addresses and passwords stolen in hack attacks and millions more that have been left exposed by incompetent website owners. However, it’s not just your email address that’s been stolen, your name will have gone with it, possibly your address and maybe even credit card (and other) data.
The stolen information is then made available for sale on the dark web and here’s a sample of the prices it can fetch
- Credit/debit card number – $5-$11
- With the CVV (3 digit) security code – + $5
- “Fullz” (card, CVV, name, address, date of birth etc.) – $30
- Bank account access – 10% of the credit balance in the account
- Online Payment Services, such as PayPal – $20-$200
But how do you know whether your information is “out there” just waiting to be abused by cyber criminals? Well, I don’t know but I know a man who does, and he’s set up a rather useful website
Have I been Pwned?
There’s a website called Have I Been Pwned. This has been created by Troy Hunt, a Microsoft Regional Director & MVP (Microsoft Most Valuable Person for developer security). After data from a major cyber incident was “found” on the Dark Web Troy decided to put a database together – in his own time & at his own cost – as a way of allowing people to check whether their data was amongst stolen information and to “keep his hand in” from a programming perspective.
The site is now a comprehensive source of information about data hacks and data loss and is simple to use. All you have to do is enter your email address to see whether you have been “pwned”
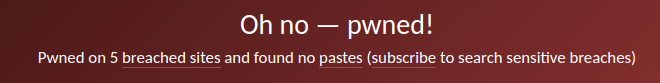
And if you have been, as shown in the image above, it will also tell you which data breach (breaches) your email address has been found in.
Not every data breach leads to passwords being available. Some databases have encrypted passwords, making them worthless to the cyber criminal. However, many don’t and, like email addresses, there are millions (over 550) of passwords available on the Dark Web.
As he’s done with email addresses, Troy has now gathered all the stolen passwords that he can find and has created another searchable database dedicated to stolen passwords.
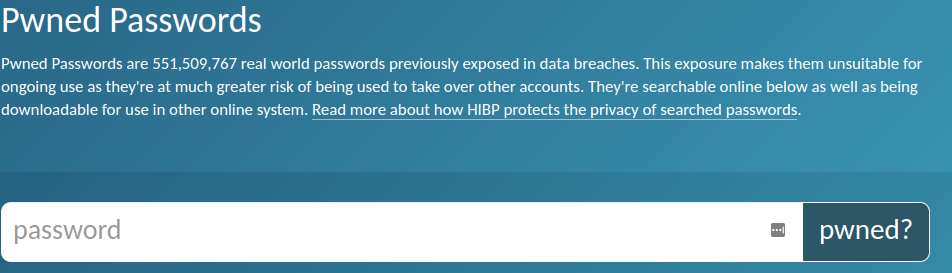
So, why is it so important to know whether your passwords are available to cyber criminals?
At this point, all the criminals have is a list of emails and and another list of passwords. They may not know which ones go together and they also don’t know which websites these email addresses and passwords relate to.
But, from our perspective, there’s a significant weakness. This comes in to play because a lot of people use the same password for many websites simply because it’s easier to remember one password than many. This use of the same password makes things a lot easier for the cyber criminals to put our data to fraudulent use.
Let’s say, for example, that the criminals target Amazon. You might have your credit card details already stored against your account so if a cyber criminal can gain access, all they have to do is change a delivery address and Bob’s their uncle.
They’ll use a “Credential Stuffing Attack” which means that they’ll load all the email addresses in to one database and the passwords in to another and start the attack. First they pick their target (Amazon in my example) and use software that will add an email address to the log-in box. They’ll then turn to different software to try all the passwords in the password database to see whether there’s a match. And once they’ve tried one email address they’ll automatically move on the next one. Once they’ve tried all combinations, and flagged those that work, they’ll move on to another site.
This sounds like a long, slow process but they’ll probably use a “Botnet” – a network of tens, hundreds or possibly thousands of hacked computers around the world that they have control over.
So, you should check “Have I Been Pwned” for both email addresses and passwords and if you’ve got a compromised password you should find the sites you use it on and change it – remembering to use a different one for each site.

Different, not similar – Password, PassWord, PAssword1960 and Pa55W0rd are NOT different to a cyber criminal. Criminals will also use these, and other variants of the world’s most popular passwords (2018’s shown in the image to the right) in their attempts to hack your accounts.
If you are concerned about your digital security, or need some help with your website, SEO or anything else online then just drop me an email, andy@enterprise-oms.co.uk , or give me a call on 01793 238020 for a free, no obligation conversation about your requirements
*Pwned – When a map designer in the online game called Warcraft beat another player he wanted to say “Player x has been owned”. Unfortunately, he mis-typed and actually said “Played x has been Pwned”. This is now a “thing”
