For many years, the security mantra has been
For many years, the security mantra has been
- Mac good, invulnerable to viruses and hacking.
- Windows bad, very vulnerable to viruses and hacking
The reason was two-fold, whilst it’s true that the Apple operating system IS harder to infect with a virus, the main reason was popularity (or lack thereof). When 97% of the world was using Windows, why bother writing viruses and other malware for the extreme minority.
The traditional Windows solution was to install an anti-virus program from one of the many vendors and, for real belt-and- braces safety, protect your internet connection with a firewall. Hopefully all would be well and good, so long as you paid your annual anti-virus subscriptions and ensured that the virus definitions were regularly updated so your anti-virus program could identify the threats and keep you safe. (Free anti-virus programs for home users did a similar job, again provided they were kept up to date)
Significantly Increased Risk of Infection
However, the upsurge in Apple popularity over recent years means that Apple devices are also targets of the cyber-criminals. And it’s not just Apple computers and iDevices that are at risk, the virus writers are also targeting Android devices, Microsoft phones and tablets and devices running Linux devices.
Anti-Virus is dead!
 Last year, Brian Dye, Senior Vice-President for Information Security at Symantec (the company behind Norton Anti-Virus solutions) said, in an interview with The Wall Street Journal, that “Anti-Virus is dead”. What he meant was that cyber criminals were now able to write malicious software faster than Norton could be updated.
Last year, Brian Dye, Senior Vice-President for Information Security at Symantec (the company behind Norton Anti-Virus solutions) said, in an interview with The Wall Street Journal, that “Anti-Virus is dead”. What he meant was that cyber criminals were now able to write malicious software faster than Norton could be updated.
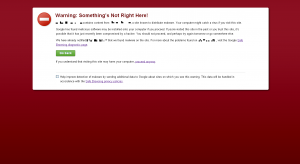
Whilst Norton, and all the other anti-virus programs, are not yet ready for the scrapheap they only detect around 45% of all attacks. As well as that rather disturbing stat, research by FireEye (A cyber-security provider) indicated that 82% of malware detected by their security solutions stays active for just one hour and 70% of threats surface just once before disappearing and being re-written to avoid detection by the AV companies.
So, what should you be doing?
 Well, I’ve said it before, but it’s always worth reiterating, security starts with education. Then you add as many layers of additional protection as you feel necessary, depending on how you use your devices and the level risk you feel you are faced with.
Well, I’ve said it before, but it’s always worth reiterating, security starts with education. Then you add as many layers of additional protection as you feel necessary, depending on how you use your devices and the level risk you feel you are faced with.
- Never open an attachment unless you are expecting one and you know, and trust, where it came from.
- Keep your Anti-Virus software up to date and continue to renew your subscriptions, it may only block 45% but that’s nearly half of all threats stopped before they have a chance to install.
- Install a security App on your phone and tablet
- Explore the new offerings from the traditional anti-virus vendors that look to protect your web browsing and protect you against spam, phishing attacks and other cyber crime threats.
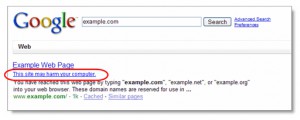
- Be alert for anything that doesn’t feel “right” and if something looks too good to be true, that offer of a full version of Microsoft Office on CD for £50.00 for example, remember, it probably is!
- Use a different, complex, password for each website that you have to log in to. An App such as LastPass will help you create passwords, securely store them and auto-complete the log-ins when you log in to those websites. (other password tools are available)
- Ensure your Social Media accounts privacy settings are set to an appropriate level
- Look at Bitdefender Safego,a free anti-scam service for Facebook and Twitter
- Remain cautious when using any internet connected device