Let’s answer the easy question first, “do I need 2FA”? The simple answer is “yes”, you do need Two Factor Authentication (2FA). Now read on to learn more about what it is, how it works and how it can secure your data and online activity
I’ve written in previous posts about passwords, hacking, identity theft and the threat to our privacy, data and businesses from cyber criminals. As you might imagine, the number of attacks is increasing, as is the sophistication.
Why are Cyber Attacks increasing
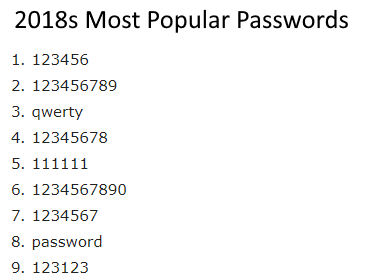
Simple! The number of websites that we log-in to continues to increase and
many people use one password across many websites. As you can see from the list on the right a lot of people use passwords that are less than ideal. The cyber criminals know this which makes it a gift for them.
Some people think they are safe because they have 3 passwords. A simple one for common sites where they don’t see a threat (posting comments to newspaper websites for example), a medium one that they use for on-line shopping and Cloud storage sites (DropBox for example) and a really complicated one for their “secure” sites, such as bank access etc.
After all, just trying to remember pWa#eeAS7uNggK49 is a challenge but if you have to remember a different one for every single website it becomes a real challenge. You might jot them down in a notebook or diary but what happens if you loose your book, or just leave it on a train. Not only have you been frozen out of your accounts (until you work your way through all those “forgotten password” routines) but your security has been seriously compromised.
Some people, like me for example, use password manager. These apps create a secure password for ever site that you log in to and make it available across desk-tops, lap-tops, phones and tablets and don’t cost very much at all. But even if you use one how secure are you, actually?

If a site that you use your super strong password on is penetrated and data stolen, your strong password is about as much use (from a security perspective) as the infamous chocolate teapot. And if you have used this super-strong password on more than one site you are at an even greater risk of becoming a victim of data theft. With more than 6,474m email addresses in the wild for cyber criminals to use and 551m passwords stolen in security hacks the criminals job gets ever easier.
Use the Have I been Pwned website to see whether your passwords have been stolen by cyber criminals or nabbed in a data breach and read more about the risk, and how the criminals use this stolen data in a previous post.
What’s the Solution
It’s actually fairly simple. It’s called two factor authentication [2FA] or multi-factor authentication. This is where another layer of authentication is required, beyond your user name and password.
In the early days of 2FA sites would send you a text with an access code so you could only log-in if you had your phone with you [and had a mobile signal]. This extra layer of security hit the cyber-criminals hard, until they realised that intercepting text messages was not particularly difficult if you were tech-savvy so something else was required.

The banks solved this problem by providing you with a device like the one to the right, this one’s from HSBC. At the website you enter your user-name and pass-code as normal, enter a PIN in the device and then enter the displayed number from the device in to your banks website. It may feel like a pain but it really does have a positive effect on the security of your on-line banking. A criminal needs a your user name/password, access to a device as well as your device PIN
Having a device for every website is pretty clunky so Microsoft and Google released authentication apps for Android and iPhones. The way they work is they generate a six digit code, as can be seen in the image on the right, and the website that you are looking to access requests this code after you have entered your user-name and password – as demonstrated in this screen-shot of my LastPass password manager.
All I have to do is launch my Authenticator App and enter the six digit password. For additional security, the code changes every 30 seconds or so
Hardware Security

The final security solution is the physical “Key” such as this one from Yubikey. This is a USB device that simply plugs in to a USB port on your computer and allows you access to secured sites – or even your computer itself.
If you are worried by your security, or need any help with your internet activity, from a new website through social media and on to other online marketing opportunities then just send me an email – andy@enterprise-oms.co.uk or give me a call on 01793 238020









